Table of Content
In today’s data-driven landscape, where change and innovation take center stage, security stands as an utmost priority. Starting from 2020, there has been an unprecedented surge in the pace of digital transformation. As a response to the disruptions caused by the pandemic, businesses across various industries are swiftly embracing cloud computing or replacing their existing ERP or legacy systems.
As per Gartner Inc., there is a projected 18.4% increase in global spending on public cloud services in 2021, and by the year 2024, over 45% of IT expenditures are expected to transition from conventional systems to the cloud.
Businesses, regardless of their size or industries are embracing migrating to the cloud to stay ahead of the curve and ensure higher scalability. Undoubtedly, there are various incredible benefits of cloud ERP systems for companies. However, the main concern is the increasing risks associated with cyber threats and data breaches.
Protecting this data is not just a matter of compliance; it's a fundamental responsibility. It's about safeguarding your reputation, your customers' trust, and your competitive edge. Considering this fact, Microsoft ensures high-security standards in their Microsoft Dynamics 365 business solutions.
In this blog, we’ll study how safe your data in Microsoft Dynamics 365 is. If you are planning to invest in this solution, this blog is for you.
Let’s study Microsoft Dynamics 365 Data Security.
Microsoft Achievements in Data Security

In 2020, Microsoft achieved recognition by Gartner as a leader in Four Magic Quadrants related to security, encompassing areas such as access management, unified endpoint management tools, cloud access security brokers, and enterprise information achieving.
Additionally, Microsoft demonstrates its commitment to cybersecurity through an annual investment exceeding $1 billion in research and development.
Their cloud security strategy adopts the “Zero Trust” framework, operating under the premise that breaches are possible and, as such, takes proactive steps to rigorously verify the security status of elements such as identity, endpoints, networks, and other resources. It uses real-time policies to limit access and reduce risks while also employing automation and machine learning for fast detection, prevention, and recovery from attacks by analyzing behavior and large datasets.
Is your data secure in Microsoft’s Azure Cloud?
All the Microsoft’s cloud offerings, including Dynamics 365, are constructed and operated within their cloud infrastructure known as Azure, which ranks as the world’s second-largest public cloud provider. Furthermore, Azure has the highest number of compliance certifications compared to any other cloud service provider.
Azure operates across more than 100 highly secure Microsoft data centers located worldwide, and each of these physical data centers boasts a multi-layered security apparatus. These security layers encompass access authorization, multiple physical barriers, various identification methods, as well as tangible security features like securely locked server racks, perimeter fencing, continuous 24x7 video surveillance, and a suite of other stringent security protocols.
In addition, Microsoft houses the Cyber Defense Operations Center, a robust cybersecurity and defense facility dedicated to safeguarding the integrity of the cloud infrastructure. Staffed by over 3,500 cybersecurity experts working around the clock, this center is responsible for real-time threat protection, detection, and response.
Microsoft's commitment to security extends further with ongoing internal exercises. Over 200 professionals are divided into two teams: the red team, tasked with attempting to breach Azure's infrastructure, and the blue team, responsible for defending against red team attacks. These exercises culminate in a process where the teams translate their findings into the Azure operational security framework, enhancing the platform's continuous threat detection and response capabilities.
Let’s explore some critical layers of Azure’s security model, which encompasses:
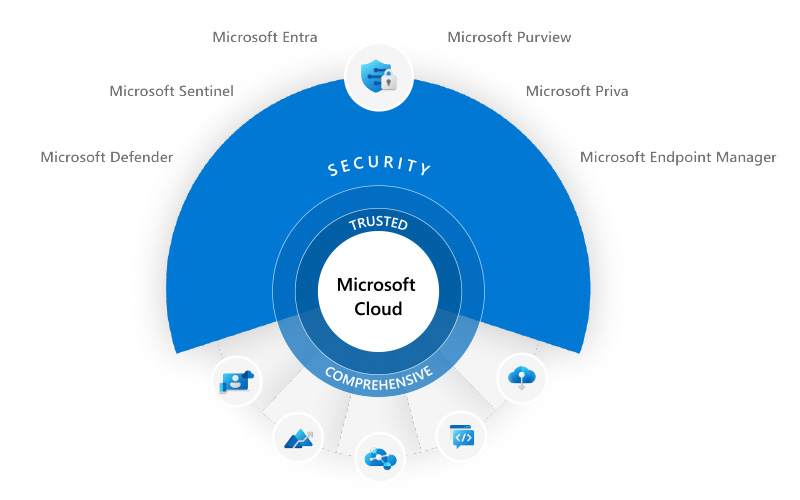
- Industry-standard encryption protocols
- Secure networks and firewalls
- Secure keys and hardware security modules (HSMs)
- Malware and ransomware protection
- Access management with multi-factor authorization
Azure provides the Azure Security Center for customers to secure their Azure-hosted solutions. It covers security management, and advanced threat protection, and allows you to set policies, manage threats, and respond to any security issues.
Microsoft Dynamics 365 security: Is your Data Safe?
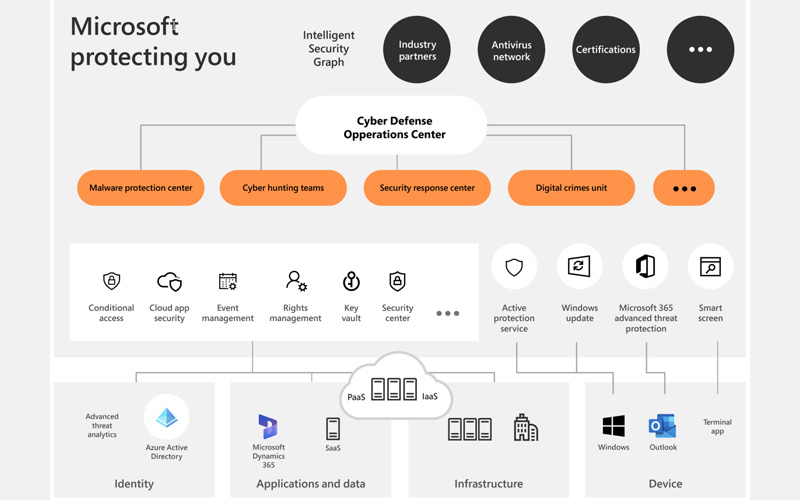
When you choose a cloud-based solution from Dynamics 365, you can have full confidence that you are gaining access to the same cutting-edge levels of security, privacy, and compliance as it is also built on the Azure platform.
Another important point to note down that when you are using Microsoft Dynamics 365 for your business operations, you maintain ownership of your data, despite it being hosted in a data center. Microsoft serves as a custodian, safeguarding your data through encryption. Notably, it led the way as the initial cloud provider to comply with ISO 27018 standards, which guarantee a spectrum of ethical standards.
This means your data and your customers' data are solely used for the services you've agreed to, and it's never shared for advertising or marketing by third parties.
Related Posts - How Microsoft Dynamics 365 Improves Your ROI?
Multi-Layered Security
Microsoft understands the critical nature of data security, and Dynamics 365 reflects this commitment with a multi-layered security approach. This approach encompasses data encryption, identity and access management, threat detection, and more. By layering these security measures, Dynamics 365 ensures that your data remains protected both at rest and in transit.
Role-Based Access Control
Role-based access control (RBAC) is a fundamental component of Dynamics 365 security. It allows you to define and control who has access to specific data and functions within the system. With RBAC, you can assign roles and permissions to users, ensuring that they only have access to the information necessary for their job function. This minimizes the risk of unauthorized access to sensitive data.
Data Encryption
Dynamics 365 employs robust encryption techniques to protect your data. Data at rest is encrypted in the database, while data in transit is secured using industry-standard encryption protocols. This ensures that even if someone gains access to your data, it remains unintelligent without the proper decryption keys.
Identity and Access Management
Identity and access management (IAM) is pivotal in preventing unauthorized access to your Dynamics 365 environment The system supports various authentication methods, including multi-factor authentication (MFA), which adds an extra layer of security by requiring users to provide multiple forms of identification before accessing the system.
Continuous Monitoring & Threat Detection
Dynamics 365 incorporates advanced threat detection and monitoring capabilities. It can identify suspicious activities, such as unusual login attempts or data access patterns, and trigger alerts or automated responses to mitigate potential threats. This proactive approach helps in preventing security breaches before they can cause harm.
Compliance & Auditing
For businesses operating in regulated industries, compliance with industry standards and regulations is crucial. Dynamics 365 offers built-in compliance features and audit trials that enable you to track changes and maintain a comprehensive record of data access and modifications. This helps you demonstrate compliance and respond to regulatory requirements effectively.
Secure Development Practices
Microsoft follows secure development practices when designing and updating Dynamics 365. Regular security assessments and patches are released to address vulnerabilities and maintain the integrity of the system. This proactive approach ensures that your Dynamics 365 environment remains secure and up to date.
Key Takeaway
Microsoft Dynamics 365 provides a robust and comprehensive security framework to protect your data. By implementing multi-layered security measures, role-based access control, encryption, identity and access management, continuous monitoring, compliance features, and secure development practices, Dynamics 365 goes the extra mile to ensure that your data is safe from both external and internal threats. When used in conjunction with best practices and user training, Microsoft Dynamics 365 can be a powerful ally in your quest to keep your data secure.
Related Posts - How to Choose the Right Microsoft Dynamics 365 Partner?
FAQ’s
1. What is Dynamics 365 Data Security?
Microsoft Dynamics 365 Data Security refers to the comprehensive set of measures and protocols implemented within Microsoft Dynamics 365 to protect your data from unauthorized access, breaches, and cyber threats. It encompasses encryption, access control, threat detection, and compliance features that work together to ensure the safety and integrity of your valuable business data.
2. How does Dynamics 365 ensure data security?
Dynamics 365 employs a multi-layered approach to data security. It includes role-based access control, data encryption, identity and access management, continuous monitoring, and compliance features. These elements collectively safeguard your data at all levels, from storage to transmission, while also controlling who has access to it.
3. How does Dynamics 365 protect against unauthorized access?
Dynamics 365 incorporates Role-Based Access Control (RBAC), which allows you to define roles and permissions for users, ensuring they only have access to the information necessary for their roles. Additionally, identity and access management features, such as multi-factor authentication, enhance access security by requiring multiple forms of identification.
4. Can Dynamics 365 detect and respond to security threats?
Yes, Dynamics 365 includes advanced threat detection and monitoring capabilities. It can identify suspicious activities, such as unusual login attempts or data access patterns, and trigger alerts or automated responses to mitigate potential threats. This proactive approach helps prevent security breaches before they can cause harm.
5. How does Dynamics 365 assist with compliance requirements?
Dynamics 365 offers built-in compliance features and audit trails that help you track changes and maintain a comprehensive record of data access and modifications. This capability is vital for businesses in regulated industries, as it allows for the demonstration of compliance with industry standards and regulations while effectively responding to audit requirements.
Related Posts - How Can Microsoft Dynamics 365 Help Your Business Grow?

Witness a scalable transformation
Experience real-time synchronisation and flexibility with a consistent view across your business.
Disclaimer– “All data and information provided on this blog is for informational purposes only. Dynamics Square / MPG Business Information Systems Pvt. Ltd. makes no representations as to accuracy, completeness, currentness, suitability, or validity of any information on this site and will not be liable for any errors, omissions, or delays in this information or any losses, injuries, or damages arising from its display or use.”

.jpg)











